Following up to our initial testing of the Meltdown patch for Windows 10, today we're looking deeper into the matter by testing a patched desktop system, by addressing the two now famous security flaws, Meltdown and Spectre, by applying the OS-level patch and a firmware update, more precisely a motherboard BIOS update.
If you read our previous article on the matter, it came within 24 hours of the emergency Windows 10 patch release intended to address the Meltdown vulnerability. We ran tests that made sense from the perspective of a desktop user and we found there was virtually no impact on gaming performance and no impact for content creators. There were however a few troubling results for NVMe storage devices, mostly impacting 4K read performance. Since then other fellow tech media outlets have published similar findings.
However the Windows patch only addressed Meltdown, and by now you’ve no doubt become familiar of the second vulnerability called Spectre. Because Spectre is the result of a fundamental CPU design flaw, it can’t be fixed, at least not entirely. The firmware update needed to correct it mitigates the problem, but doesn’t completely address the vulnerability.
This is still primarily an Intel CPU flaw. AMD's official word is that one of the two Spectre variants doesn’t impact them at all, while the one that does is easily resolved by a software update that shouldn’t impact performance in any meaningful way. Variant "three" which is Meltdown, doesn’t impact AMD at all. We've yet to properly test any AMD CPU ourselves, but this is based on the official information we have so far.
Since publishing the Meltdown benchmark we now have access to BIOS updates that deliver a microcode update which will mitigate the Spectre flaw on Intel’s latest Z370 platform. The update changes the behavior of Intel’s branch prediction to be less aggressive. This will likely mean less effective branch prediction and that means reduced IPC as the execution pipelines wait for memory access more often.
Of course, we'll get to the benchmarks in a moment but before we do here are a few additional notes. As of writing, the only motherboard manufacturer to release an update is Asus and so far they’ve only addressed their Z370 series of motherboards. In order to complete this test we rushed out the door and purchased an Asus TUF Z370-Plus Gaming.
Once we had that on hand, we benchmarked the Core i3-8100 without the Windows update, then tested a second time with the Windows patch applied, and then a third time with the Windows update plus the latest BIOS which includes the microcode update. We’ve included some updated Core i7-8700K benchmarks as well.
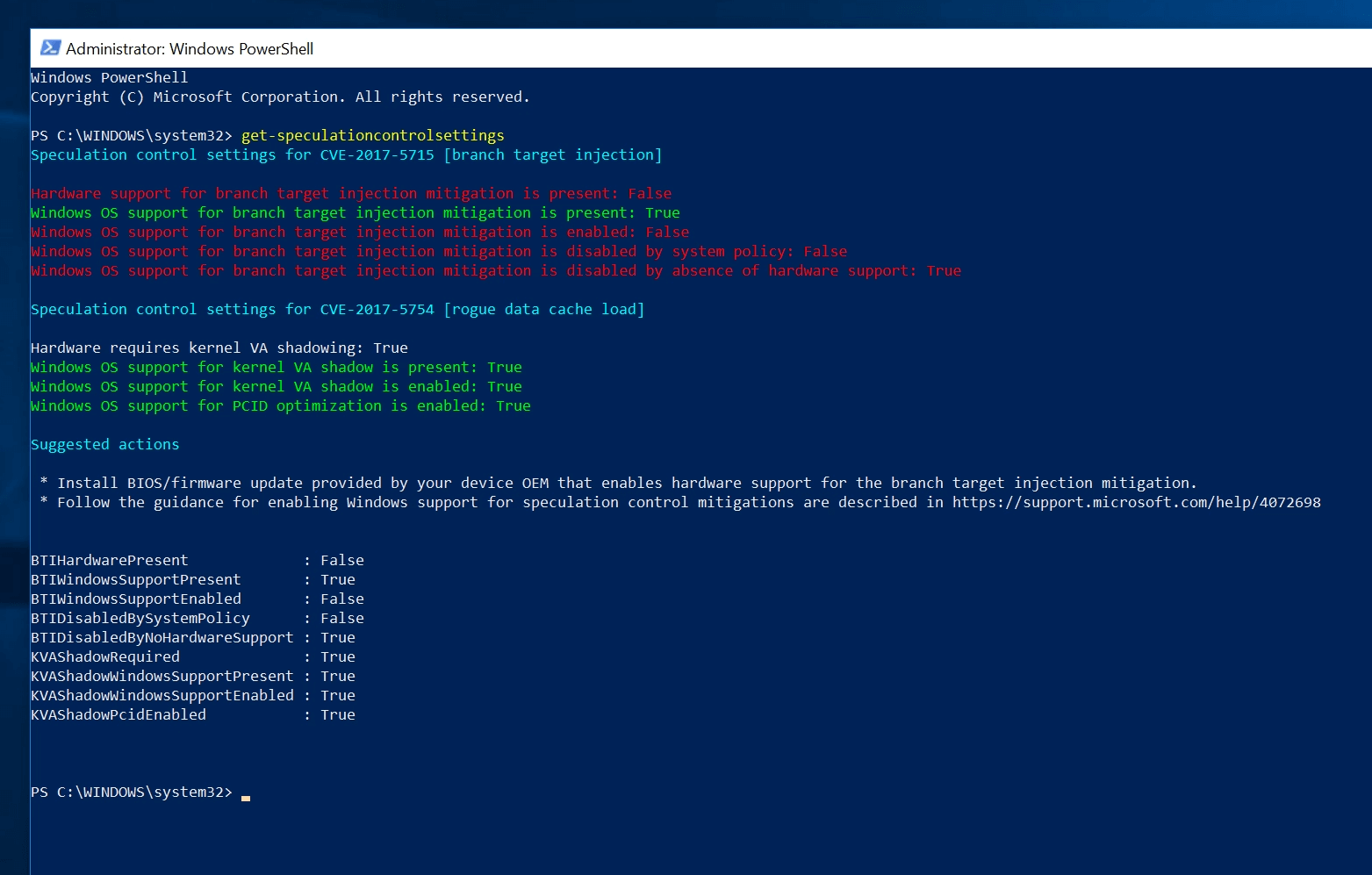
For verification, once you’ve installed the Windows update you can install a PowerShell script called Speculation Control which will allow you to check if the update has been properly applied by running the command "Get-SpeculationControlSettings". With just the Windows update which addresses Meltdown this is what you should see, all three requirements for the Meltdown, a.k.a. Rogue data cache load are greenlit and set to ‘True’:
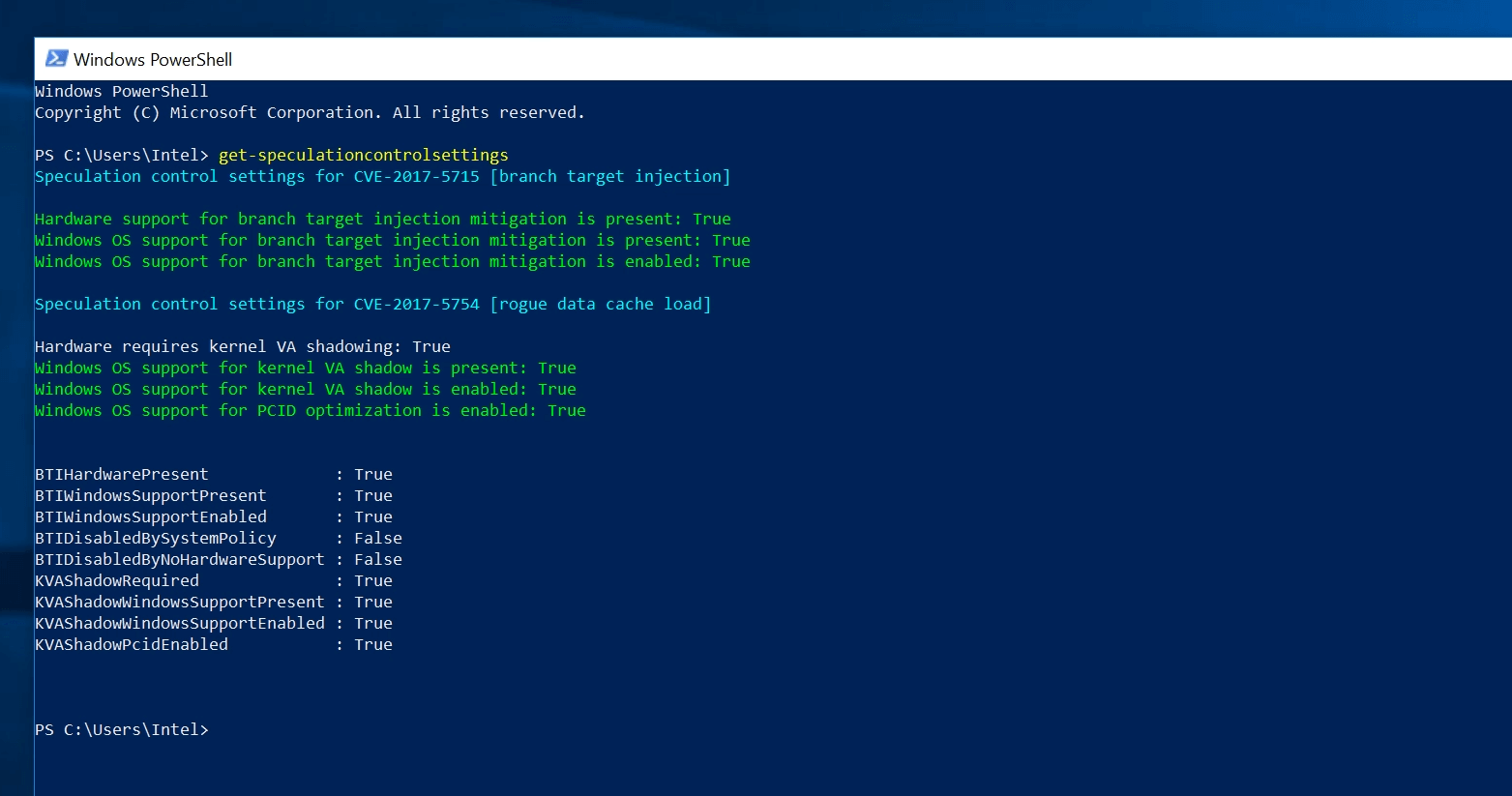
For the branch target injection (Spectre) vulnerability only OS support is present, but not yet enabled as we still require the microcode update. Once the BIOS has been updated with the required version this is what you should see:
With that brief update, it’s time to run some tests, starting with the Core i3-8100 results first. Note that all results are based on an average of at least three runs.
Benchmarks
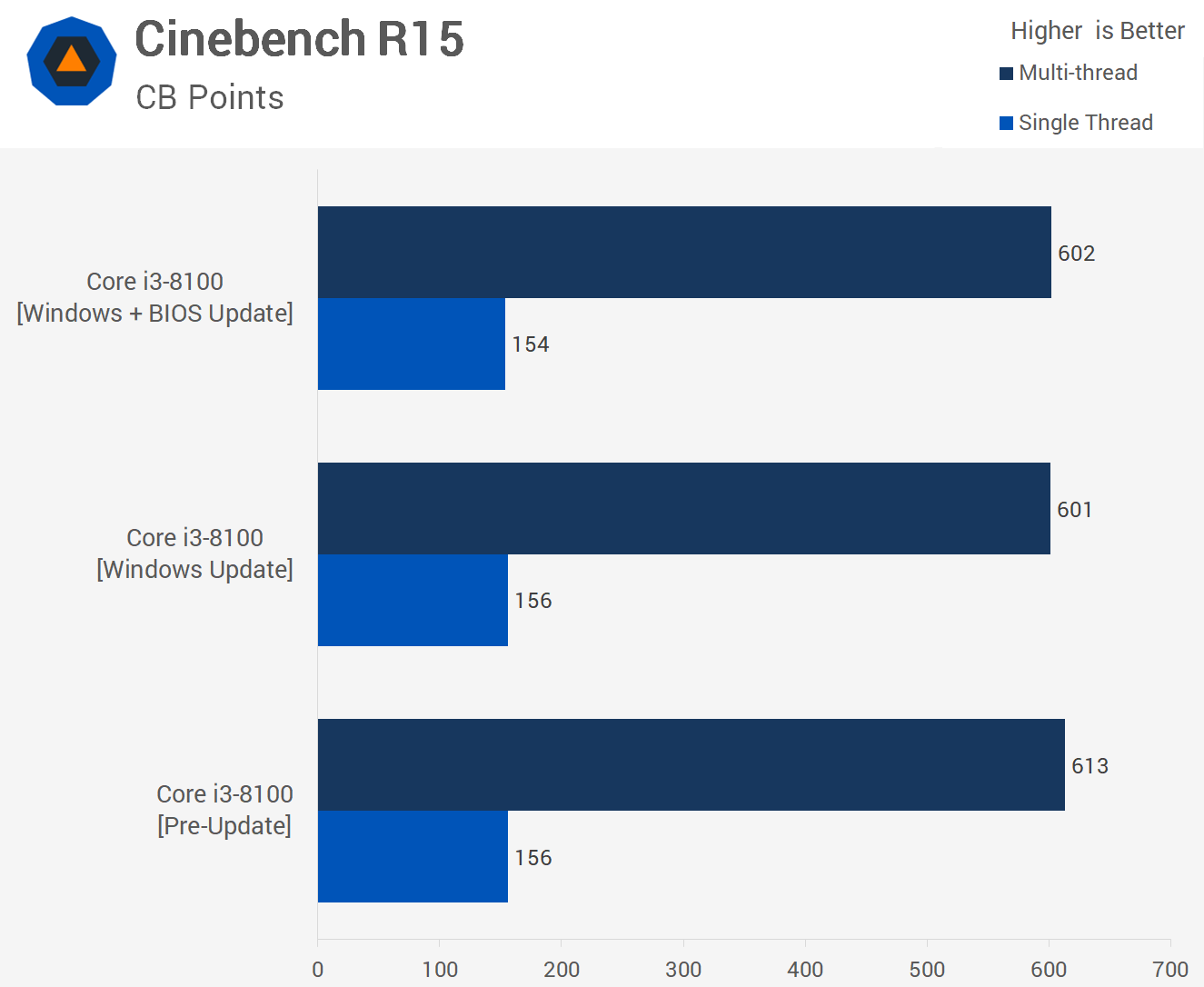
First up we have the Core i3 Cinebench R15 results and very little has changed here, from the pre-update we see less than a 2% reduction in multi-thread score and 1% for the single thread test, so that’s pretty well within the margin of error.
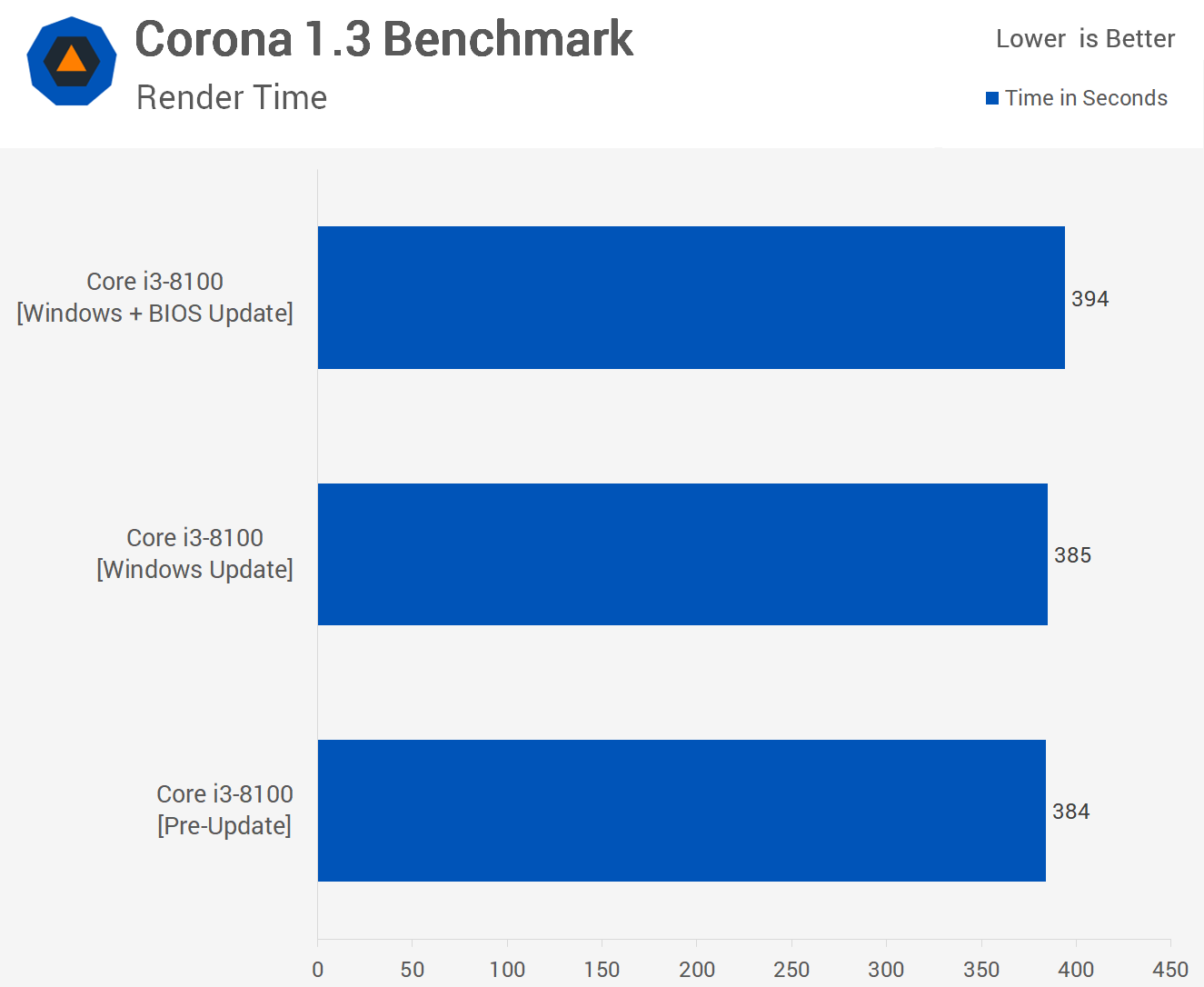
Now this is a little more interesting, the Windows patch plus BIOS update was consistently 3% slower than the previously tested configurations. Please note lower is better for this test as we’re measuring the time it takes to complete a render. So the BIOS update cost us 9 seconds but as I said overall a very minor reduction in performance.
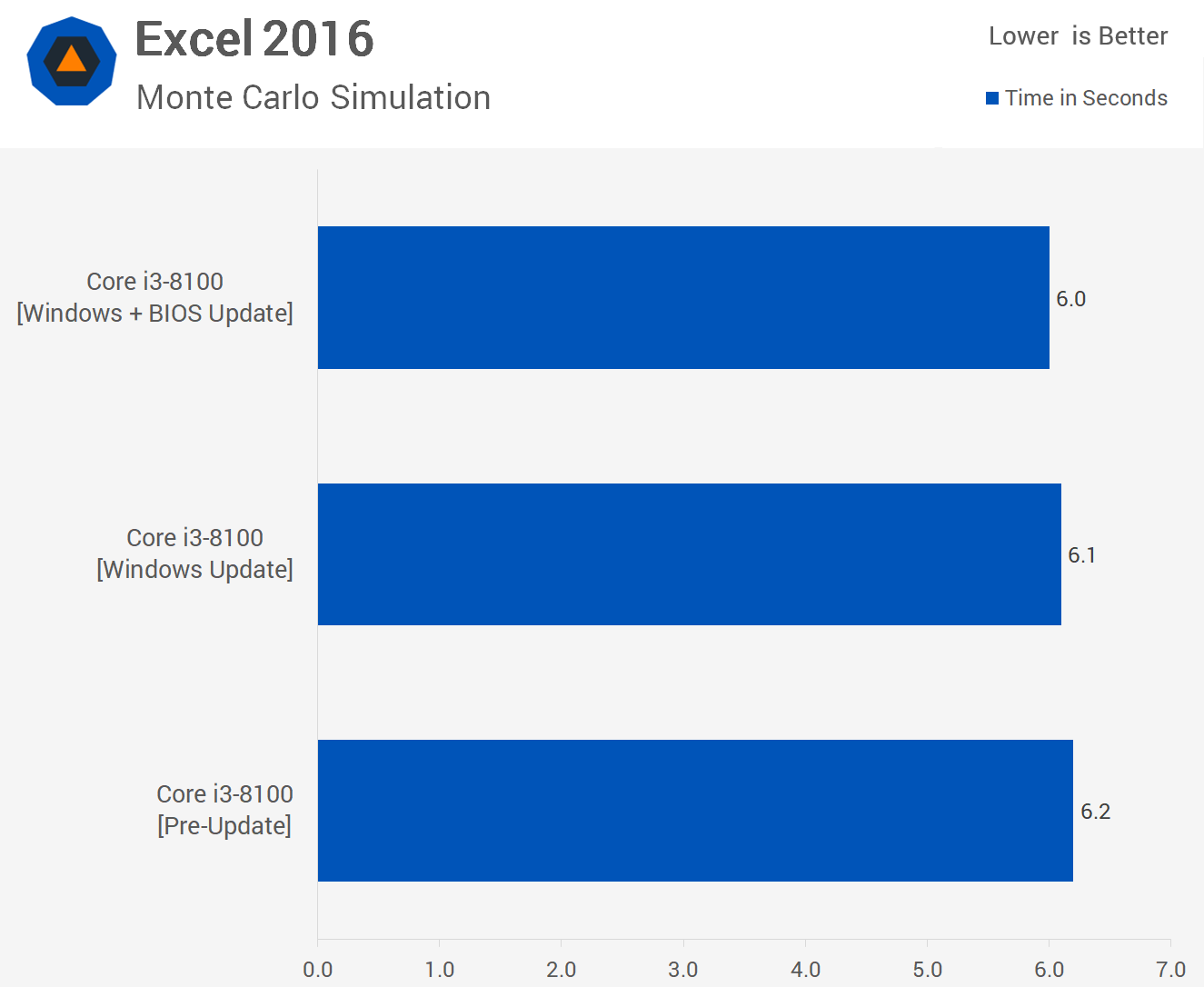
Once again the Excel workload goes unchanged, we see the same 6 second completion time, so nothing to report here.
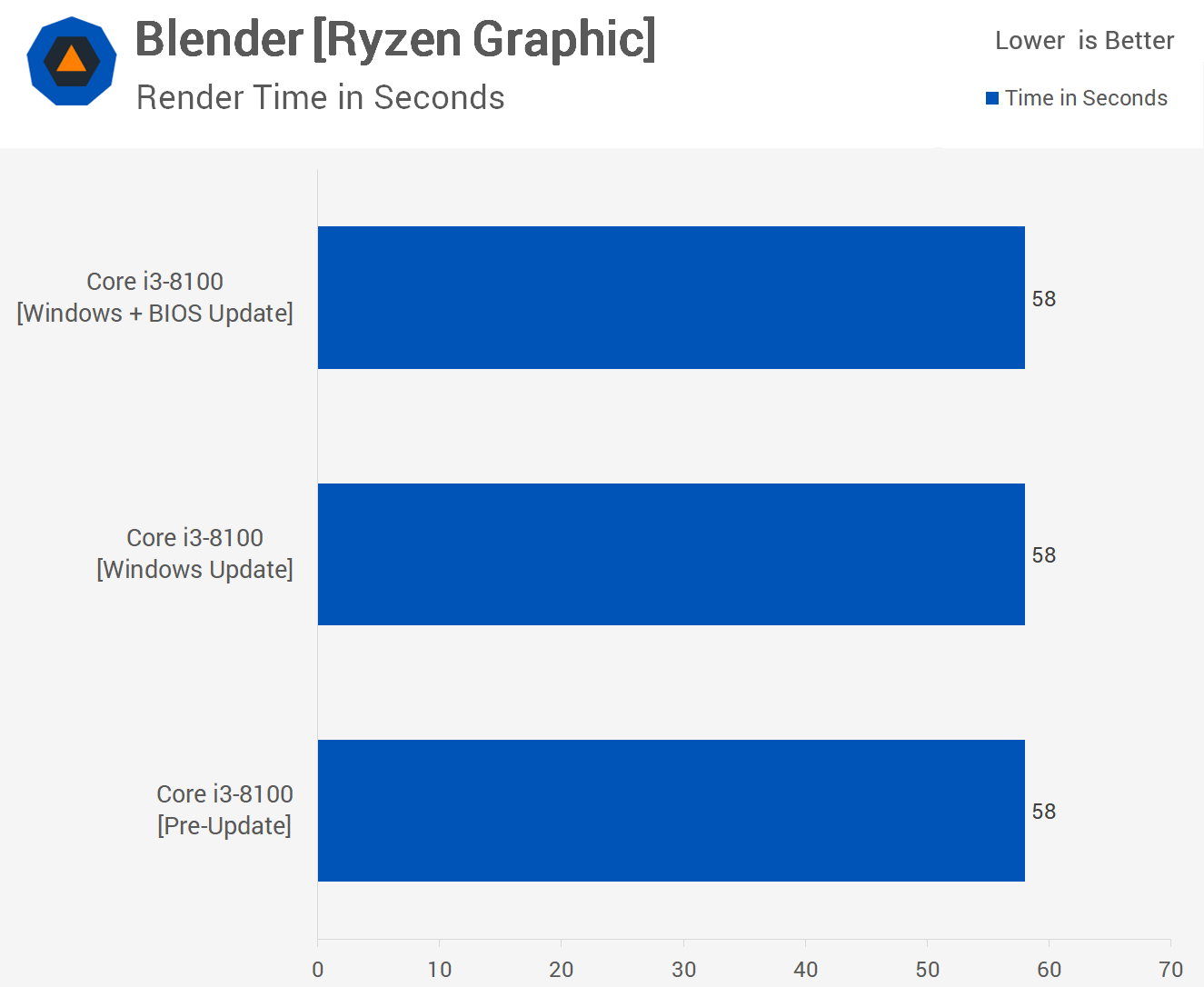
Moving on we find much the same with the Blender render test, all configurations took 58 seconds to complete the test.
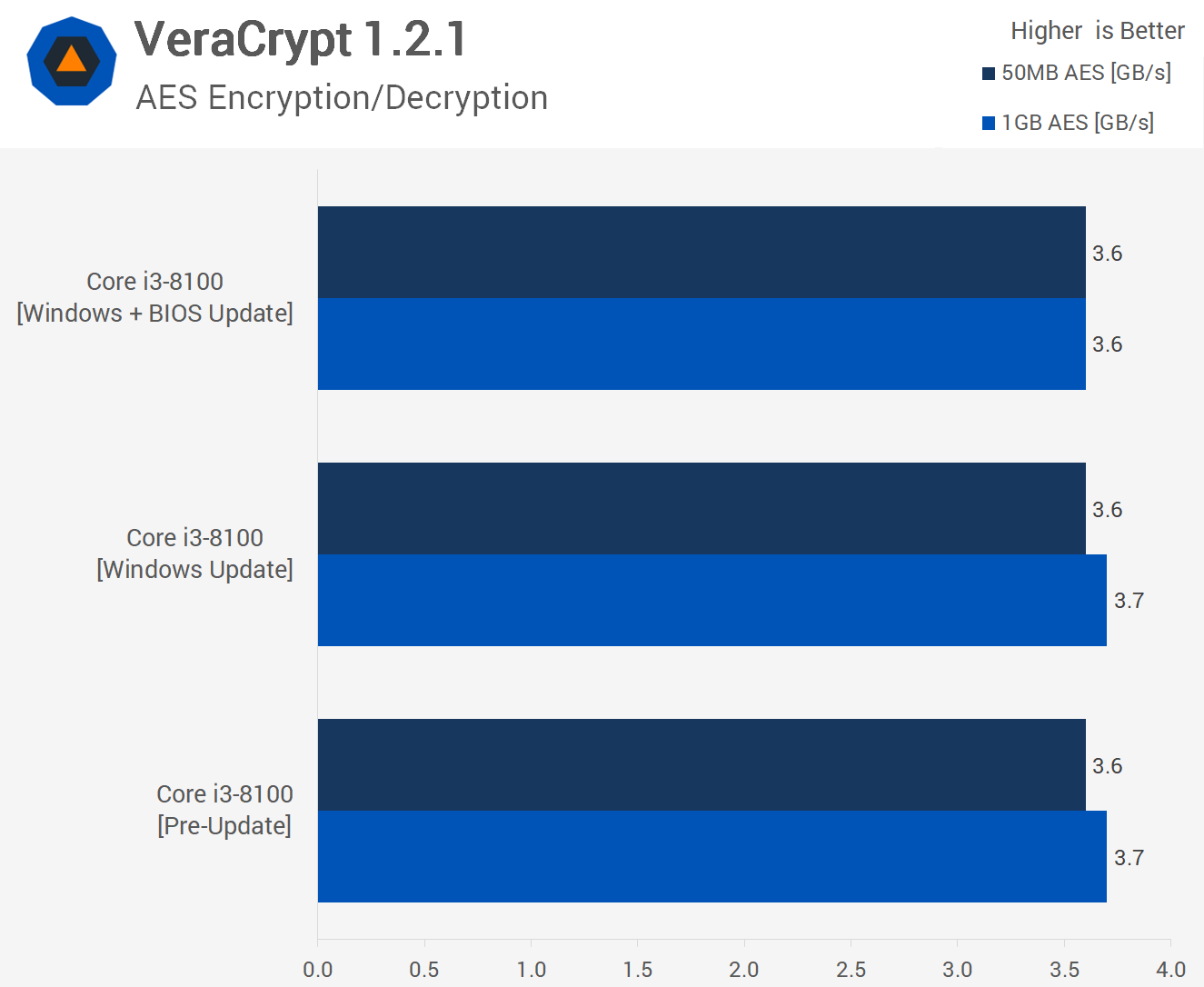
We also find no real performance difference when testing with VeraCrypt, the AES encryption and decryption results are all much the same.
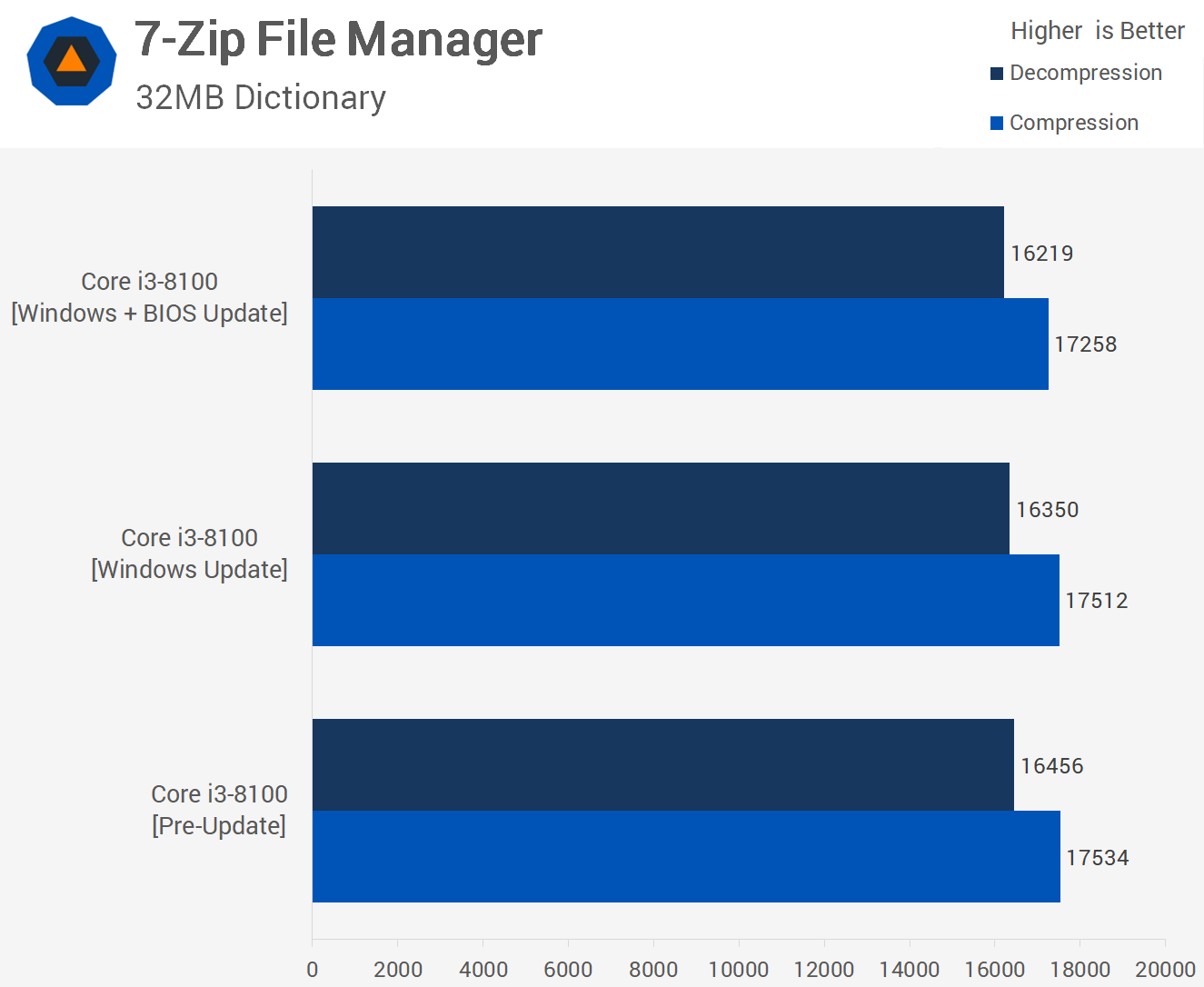
Next up we have 7-zip and here we see no noticeable decline in performance with the windows and BIOS updates applied.
Source : https://www.techspot.com/amp/article/1556-meltdown-and-spectre-cpu-performance-windows/page1.html